Every user of Tulane University's information systems resources is responsible for protecting the confidentiality, availability and integrity of the University's information assets. The Information Security Strategy supports and coordinates our university community's efforts to secure Information and Information Systems from unauthorized access, disclosure and disruption. The document outlines information classification; roles and responsibilities for protecting information; and provides a high level strategic overview of administrative, operational and technical controls that should be implemented to safeguard the University's information assets.
Summary of control requirements:
- Implemented controls should ensure the availability, integrity and confidentiality of the University's information resources.
- Roles and responsibilities for information use should be appropriately segregated to ensure users have access to information on a need-to-know basis only.
- Audit logs and trails should be maintained for all applications and systems that handle and maintain sensitive University information.
Asset Classification
To assist in the appropriate handling of information, a sensitivity classification hierarchy should be used throughout Tulane University. This sensitivity classification system ensures consistent handling of information regardless of form, mode of transmission or storage.
The information classification categories are:
- Confidential – Covers sensitive information about individuals and the University. It requires a high level of protection against unauthorized use, disclosure, modification and destruction.
- Internal Use Only – Covers information that requires protection against unauthorized disclosure, modification, destruction, or use, but the sensitivity of the information is less than that for confidential information.
- Unrestricted – Covers information that can be disclosed to any person inside or outside the University. Although security mechanisms are not needed to control disclosure and dissemination, they are still required to protect against unauthorized modification and destruction of information.
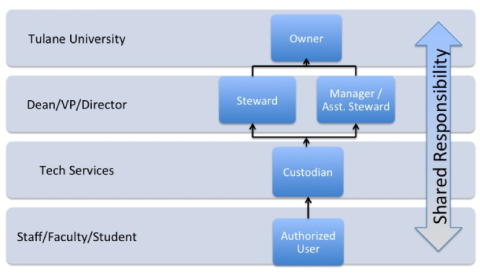
Roles and Responsibilities
As a member of the University community, you share in the responsibility for protecting information resources for which you have access or custodianship. In addition, there are particular responsibilities assigned to specific groups.
These specific groups are:
- Owner – The University is considered the OWNER of all University information.
- Steward/Assistant Steward – Those members of the University community who have the primary responsibility for a particular subset of information and perform the duties of the information owner on behalf of the University.
- Custodian – They are in physical or logical possession of information and/or information system assets and are responsible for the day-to-day operations, maintenance and safeguarding of those assets.
- User – This includes all University community members who are authorized to use any University information resource.